Business
How Digital IDs are streamlining everyday tasks for millions
We’ve recently just hit a huge milestone: our Digital ID apps have had 14 million global downloads. Businesses and individuals are increasingly using Digital IDs. In fact, experts have predicted that the number of digital identity verification checks will surpass 70 billion by the end of 2024. This blog explores how our Digital IDs are making people’s lives easier and more secure. But first, what is Digital ID? Instead of using a physical document, such as a passport or driving licence, a Digital ID is a way for people to prove who they are on their phone. Creating
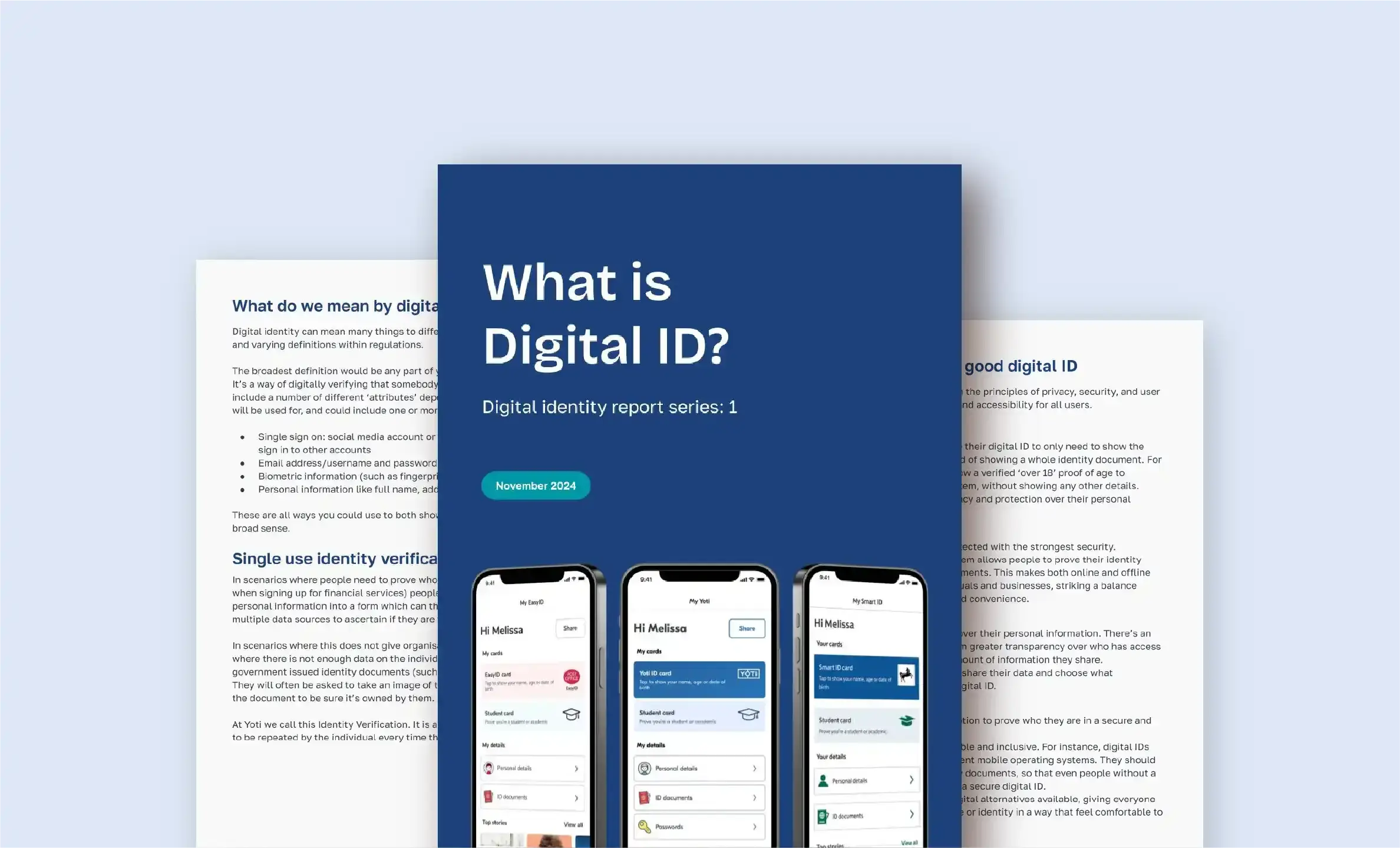
Yoti Digital Identity Report 1 - What is Digital ID?
Welcome to the first report of our new series on Digital Identity. This report focuses on ‘what is digital identity’, delving into the different definitions of the term. Digital Identity is becoming an increasingly adopted, implemented and discussed. As such it is important to understand the difference between different definitions. Download our first digital identity report – What is Digital ID? – below. No personal details, ID or data is required. Our second Digital ID report – on the value of Digital ID to businesses – can be found here. Download
’Tis the season to be thrifty: UK shoppers hunt out Christmas bargains on eBay, Etsy and Vinted, but scam fears linger
More than half of young people have been scammed themselves or know someone who has been scammed via secondhand marketplaces A quarter of Brits fear falling victim to online scams London, UK – 20th November 2024 – As the cost of living crisis continues to bite, new research from digital identity company Yoti (carried out by Censuswide) reveals that UK shoppers are tightening their belts this festive season, with 65% turning to online marketplaces in search of affordable Christmas gifts on sites such as eBay (46%), Etsy (27%), Vinted (22%) and Facebook Marketplace (18%). However, while bargain-hunting
How Yoti developed over 70 integrations in 9 months
“With the average business using over 130 software products, forward looking SaaS providers like Yoti are focused on connected experiences and making integrations a core competency.” Marcus Edgington VP of Product, Prismatic Prismatic is the world’s most versatile embedded iPaaS, helping B2B SaaS teams launch powerful product integrations up to 8x faster. Learn how Yoti used Prismatic’s embedded integration platform to bring our integrations to life. So far, we have over 70 integrations for businesses to choose from. That’s more than any other identity company. Using the Prismatic platform, we now build an integration in two weeks
How accurate is facial age estimation?
“How accurate is it?” is the first question regulators, businesses and users tend to ask about facial age estimation. To date, we have mainly presented the technology’s Mean Absolute Error (MAE) as a proxy for accuracy. It’s an intuitive way to understand how accurate a model is. We can say it’s accurate to 1.3 MAE for those aged between 13 and 17 years or 2.5 MAE for those aged between 6 and 70 years. However, the answer is slightly more complicated. Following the COVID-19 pandemic, many people will be more aware of the terms ‘true positive’ and ‘false negative’
How the University of Sheffield uses Yoti to complete right to work checks in just 5 minutes
“With Yoti’s solution, we are delivering an efficient, accurate and streamlined right to work process; improving the overall candidate experience and meeting compliance with ease.” Rachael Eustice and Jo Schofield HR & Recruitment Services The university of Sheffield is renowned for the excellence, impact and distinctiveness of their research-led learning and teaching. We helped them: Make their onboarding processes more efficient for both successful candidates and the hiring department. Enhance the candidate experience while maintaining the highest levels of compliance. Solution: Right to work Industry: Education Read the case study